Cyber criminals will say or do whatever it takes to gain access. We must do whatever it takes to defend against it.
Executive impersonation provides cyber criminals with unlimited opportunities to try and lie, cheat, and manipulate their way inside of your business. In this article, we’ll be taking a deep dive on what executive impersonation is, how the attacks work, and two practical ways on how your small enterprise that uses Microsoft 365 can protect itself against them, no matter what entitlement level or subscription you currently use.
What is executive impersonation / executive fraud?
Executive impersonation, or executive fraud, has many names, but it all comes down to a simple definition: Someone is fraudulently pretending to be someone from inside your company. Their intentions are almost certainly malicious, and they have you in their sights. Executive fraud is a targeted type of attack but is often automated. We’ll get more into that later.
How do Executive Fraud attacks work?
Malicious actors (hackers, bad guys, whatever floats your boat) use specialized tools to scrape information from public sources, like LinkedIn and company websites. The tools compile this data into a database, building a profile on your company. Once a sufficient profile has been built, the malicious actor (or the tool, automatically by itself) will use the information from their database to launch targeted attacks. One of the most simple and entry-level attacks that can be launched with this publicly scraped info is Executive Fraud.
These malicious actors and their automated tools can launch thousands of attacks like this per day. All the attackers must do is let their tool run by itself and wait some someone to respond to their e-mail – or nibble on the bait. Hence, the name “phishing”.
The more information that an attacker has on your company, the more sophisticated the attacks can become. Intelligent attackers will use the executive’s identity to extract non-public information from employees at the company and use this information to further advance the sophistication of their attack.
Ultimately, the attacker’s goal is usually to extract a ransom payment from you, sell your information to the highest bigger on the dark web, or commit corporate espionage.
How to block executive fraud.
NOTE: If you’re not an IT Professional, have your IT Department handle this for you by sending them this article.
Option 1: Implement User Impersonation Protection in anti-phishing policies in Microsoft Defender for Office 365
(For Microsoft 365 customers without access to Microsoft Defender for Office 365, such as M365 Business Standard or E3)
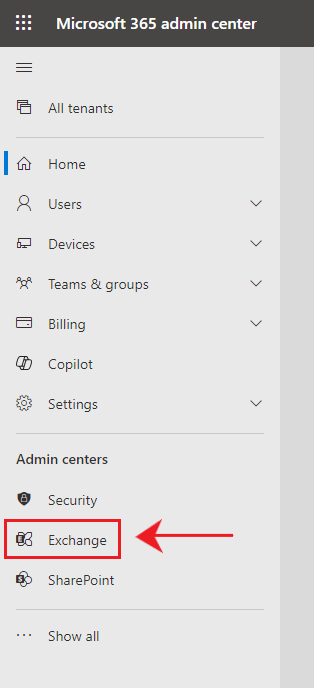
Step 1. Login to your Microsoft 365 Admin portal (https://admin.microsoft.com)
Step 2. Navigate to “Exchange Admin Portal”, a new tab will open
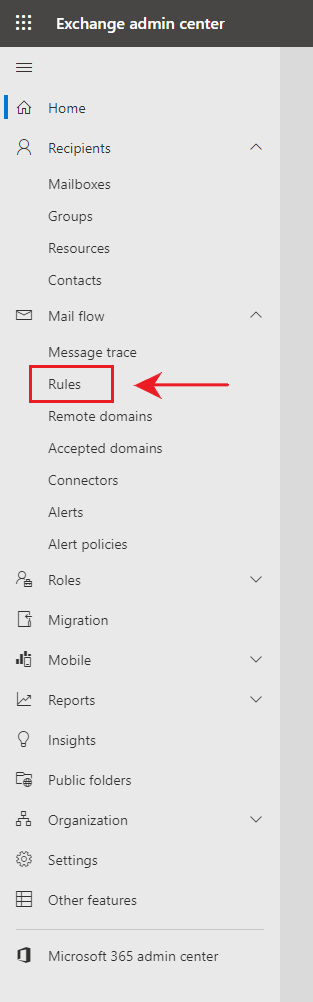
Step 3. On the left navigation pane, click “Mail Flow” > “Rules”
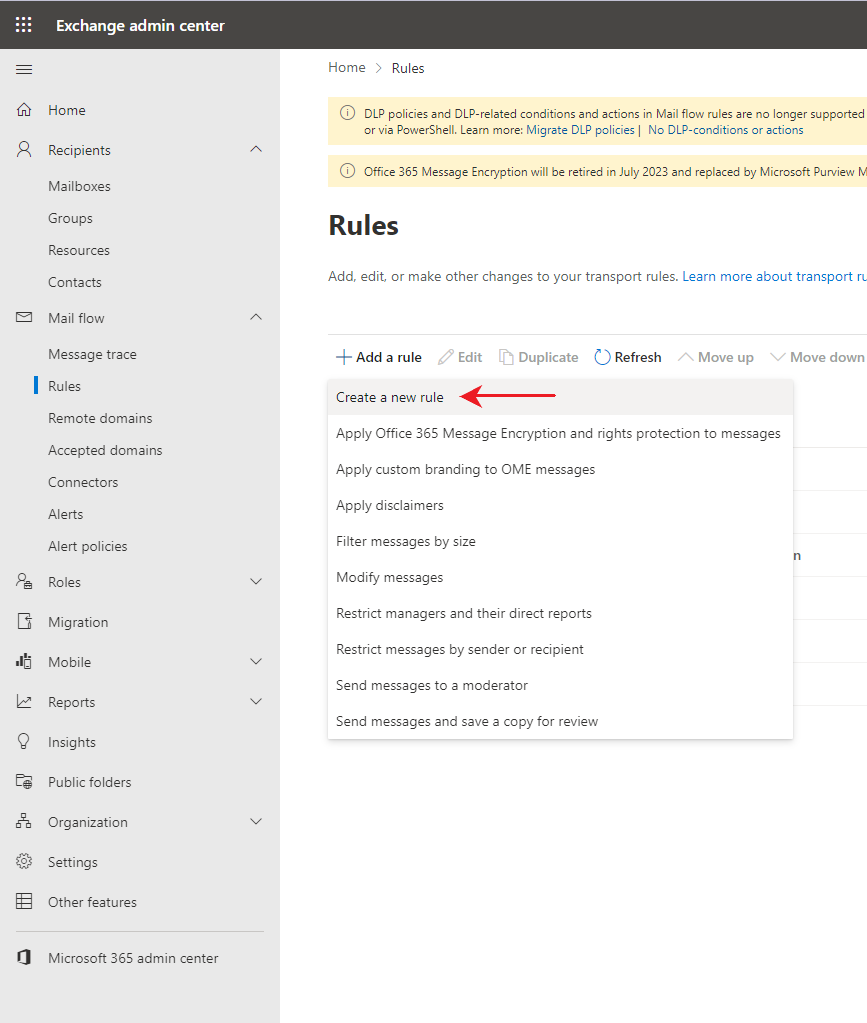
Step 4. Click “Add a rule” > “Create a new rule”
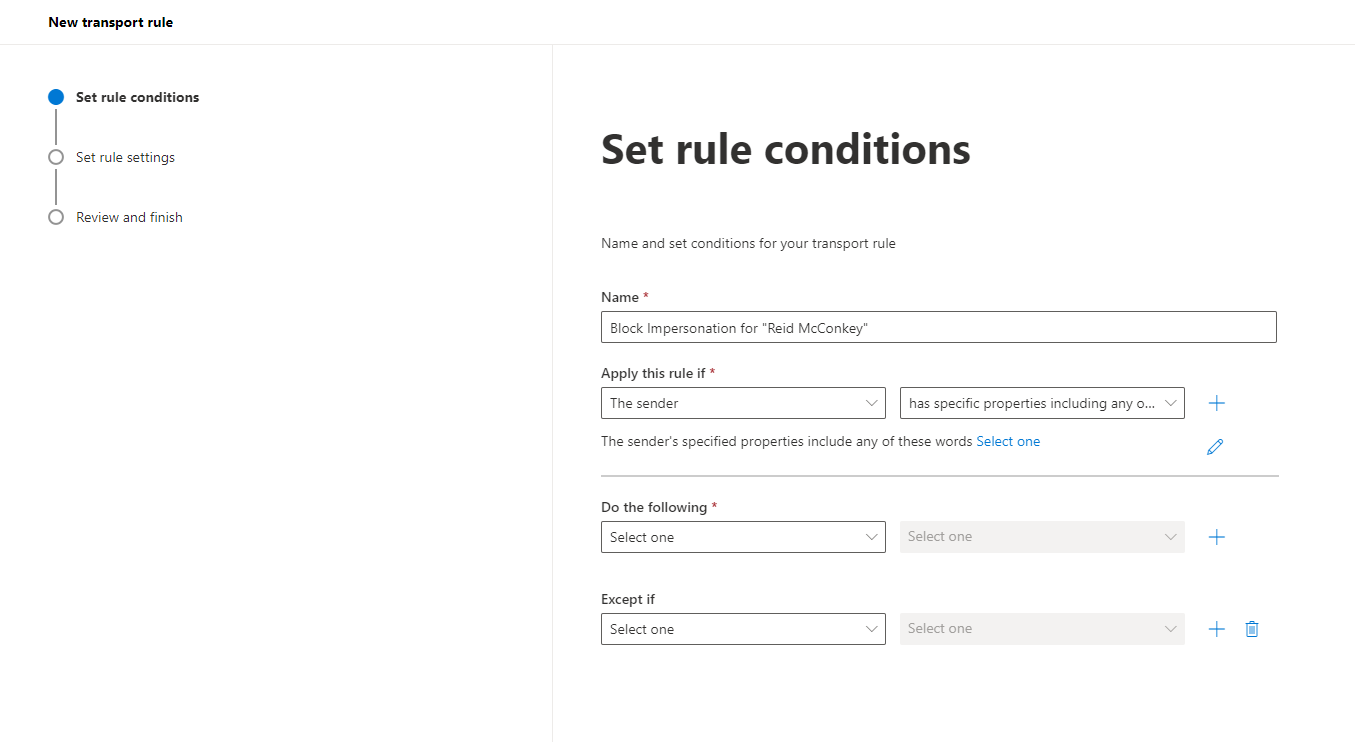
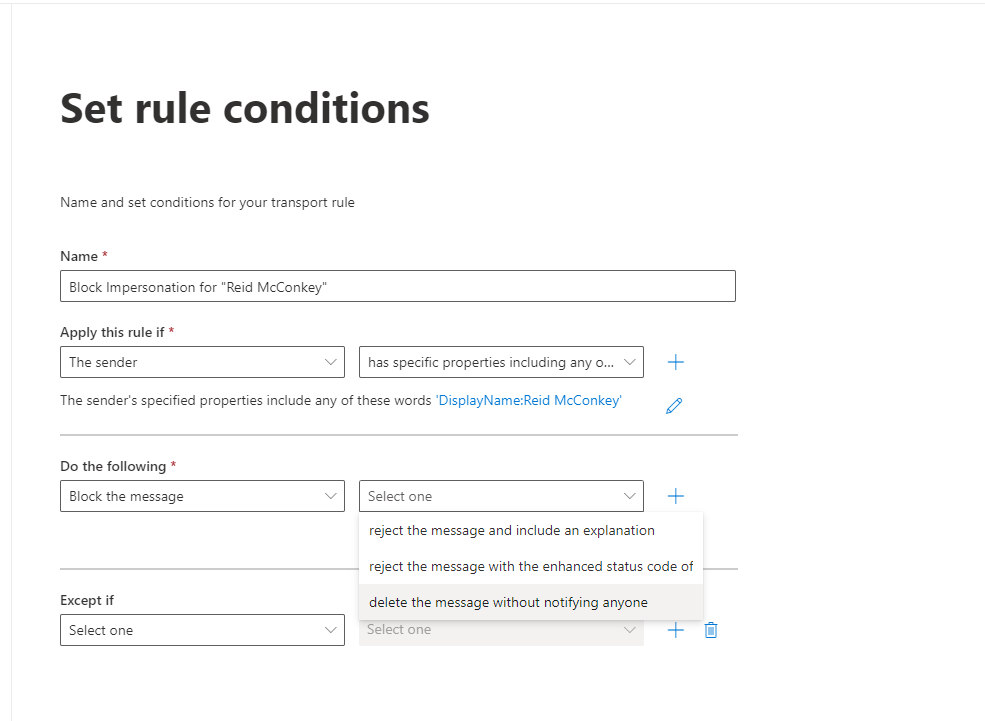
Step 5. Give the rule an appropriate name. Apply this rule if “The Sender” “has specific properties including any of these words” > A new tab will expand:
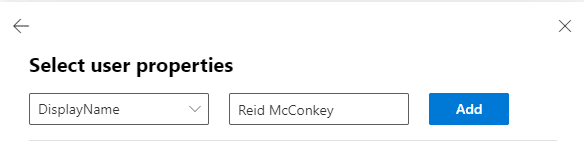
Step 6. Under “Select user properties” select “DisplayName”. For the value, enter the name of the executive that is being impersonated. For this example, we used our CEO, Reid McConkey:
Step 7. Click save and return to the main rule creation pane. Under “Do the following” select “Block the message” and configure and rejection settings you want. We recommend “delete the message without notifying anyone.”
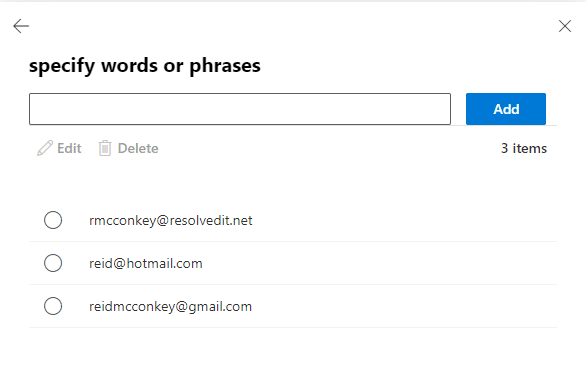
Step 8. Configure exceptions for the real executive’s e-mail addresses to ensure they won’t be blocked. Set “Except if” to “The Sender” “address includes any of these words” and enter in the executive’s legitimate e-mail addresses, including any personal addresses or secondary corporate e-mail addresses they may send e-mail to the company from.
Step 9. Click Save.
You’re done – going forward, anyone who e-mails your domain with the same display name as your executive, it will be automatically blocked. This obviously has some potential flaws, especially if your CEO’s name is James Jones – but it’s free, so can you really complain?
Option 2: Create a Microsoft Exchange Mail Flow Rule to block matching Display Names
(For Microsoft 365 customers with access to Microsoft Defender for Office 365, such as M365 Business Premium or E5)
Step 1. Login to your Microsoft Defender portal at https://security.microsoft.com
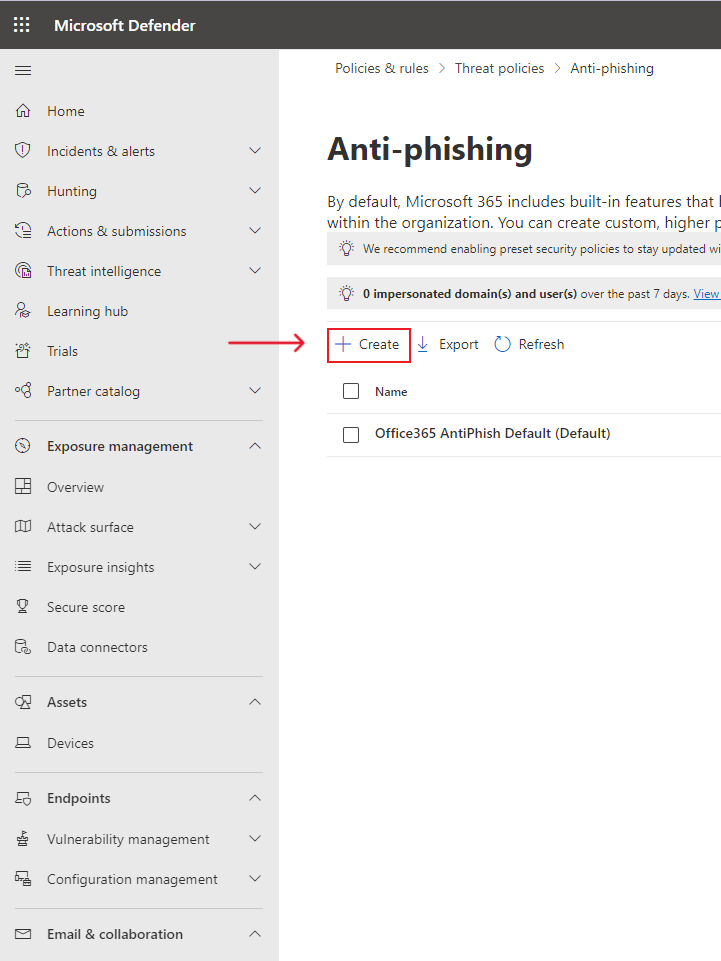
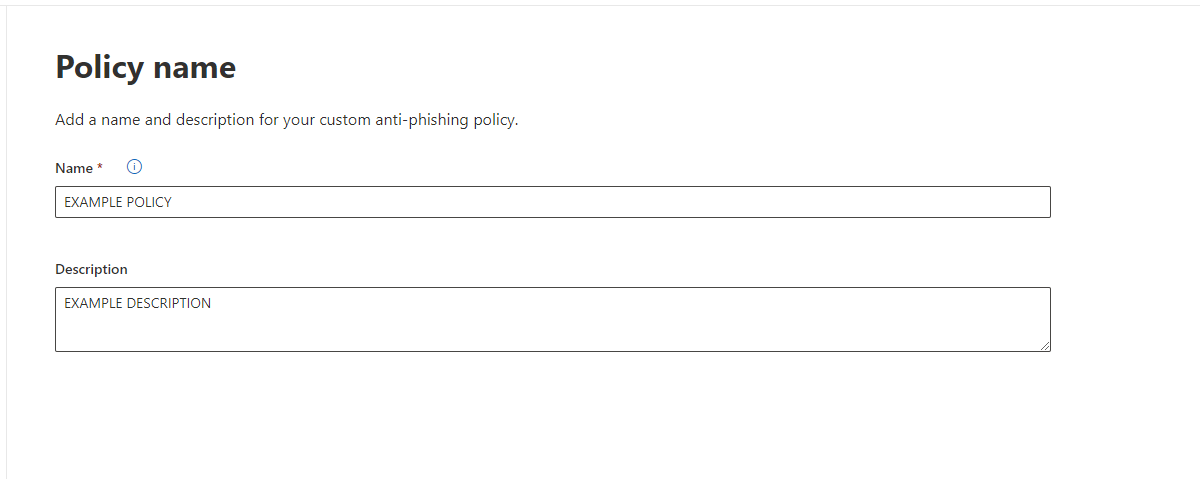
Step 2. Go to the anti-phishing page: https://security.microsoft.com/antiphishing and edit your existing anti-phishing policy. If a non-default policy doesn’t already exist, click “Create” to open the new anti-phishing policy wizard. Name it appropriately then click Next.
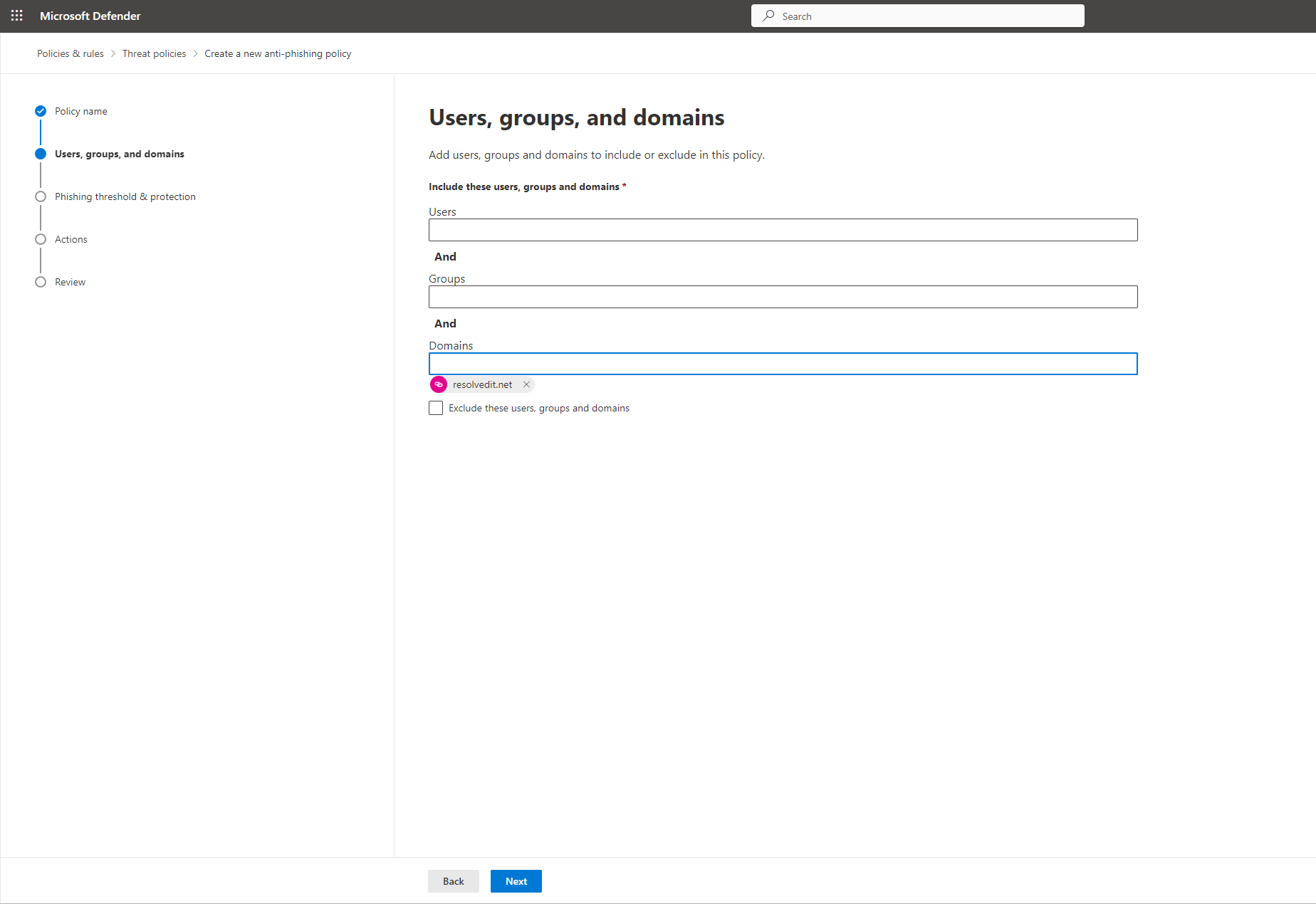
Step 3. Identify the internal recipients that the policy applies to. Select your entire domain and click Next.
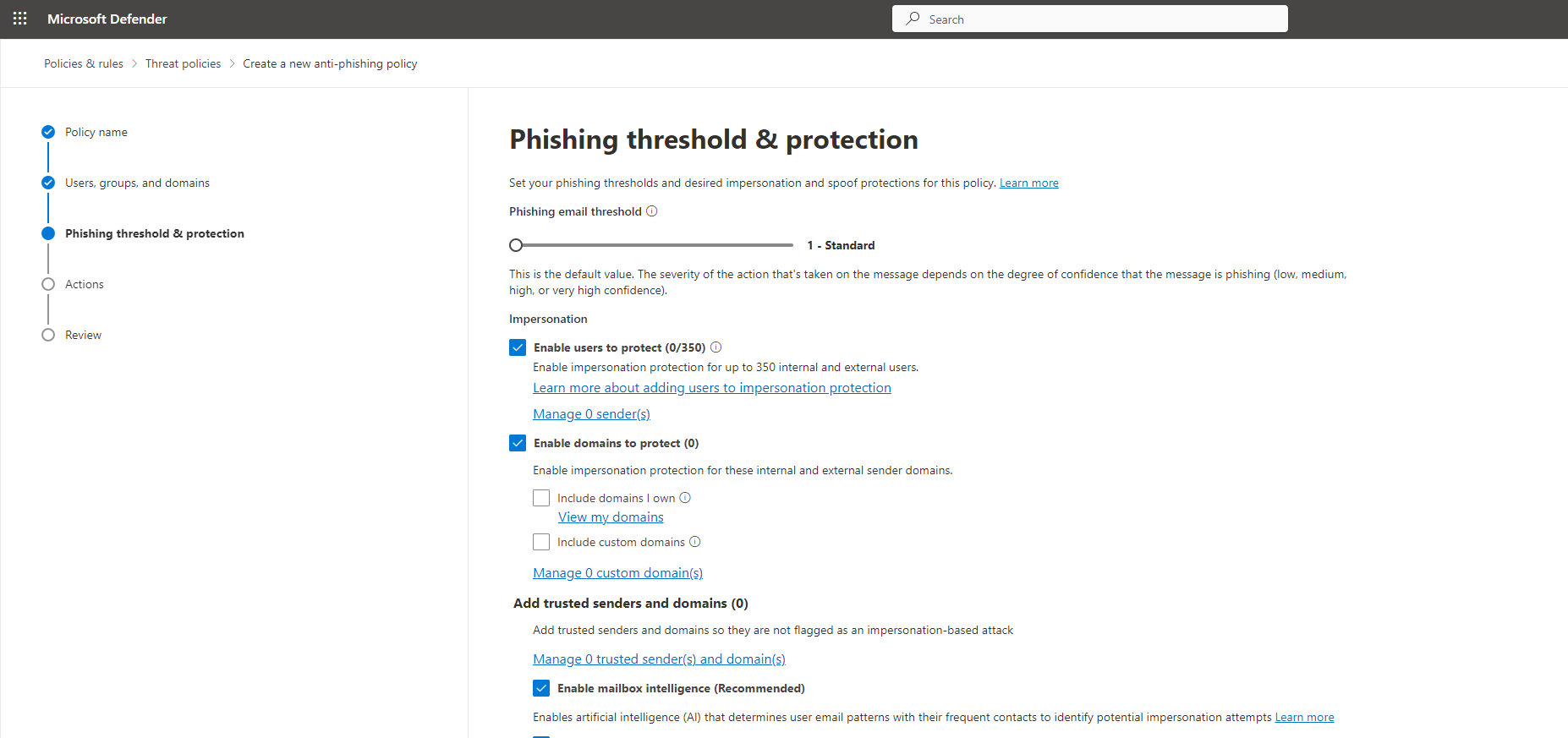
Step 4. Under “Impersonation” check “Enable users to protect” > click “Manage 0 sender(s)” and add your executive users to this list.
Step 5. Optionally, enable domain-wide protection and add trusted senders and domains. It is also highly recommended that your IT department maintain a whitelist of trusted senders to avoid legitimate mail being caught in the spam filter. We also recommend enabling spoof intelligence.
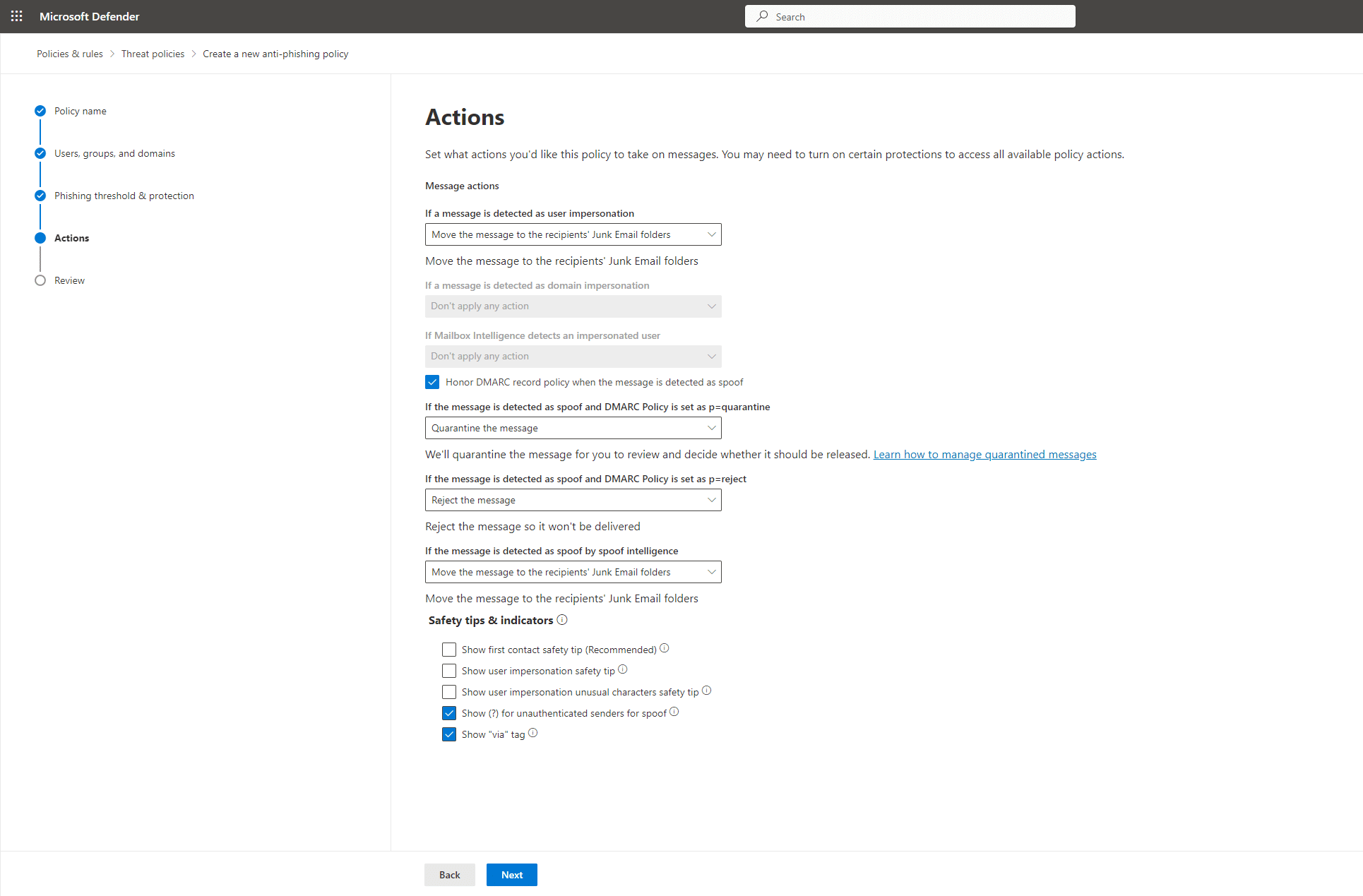
Step 6. Click next. Configure how strong you want these policies to be. We recommend starting out by simply moving the message to the recipients’ junk folders. If you’re not an IT professional, leave the rest of the settings alone. If you are an IT professional, use your own discretion here.
Step 7. Review & submit your new policy. Make sure it’s turned on. Keep an eye on the mail flow log for any e-mails that are being flagged by this, and make sure they aren’t legitimate senders.
Great – I’ve blocked all executive fraud for good… right? (Conclusion)
Well… not totally accurate. I wish it were true, but these policies are good for blocking only a good portion of executive fraud e-mails, not all of them. This means that employees still need to be trained on how to spot these types of threats with regular cybersecurity training, and safeguard policies need to be put in-place to ensure requests are legitimate.
As AI and other more sophisticated impersonation methods become more prevalent, this problem will only worsen. If there’s one thing you take away from this article, it’s this: You can and should be doing the above actions to block a good amount of the volume of these attacks, but training and good operational security in the form of safeguard policies are still mandatory.
Cyber criminals will say or do whatever it takes to gain access. We must do whatever it takes to defend against it.
Executive impersonation provides cyber criminals with unlimited opportunities to try and lie, cheat, and manipulate their way inside of your business. In this article, we’ll be taking a deep dive on what executive impersonation is, how the attacks work, and two practical ways on how your small enterprise that uses Microsoft 365 can protect itself against them, no matter what entitlement level or subscription you currently use.
What is executive impersonation / executive fraud?
Executive impersonation, or executive fraud, has many names, but it all comes down to a simple definition: Someone is fraudulently pretending to be someone from inside your company. Their intentions are almost certainly malicious, and they have you in their sights. Executive fraud is a targeted type of attack but is often automated. We’ll get more into that later.
How do Executive Fraud attacks work?
Malicious actors (hackers, bad guys, whatever floats your boat) use specialized tools to scrape information from public sources, like LinkedIn and company websites. The tools compile this data into a database, building a profile on your company. Once a sufficient profile has been built, the malicious actor (or the tool, automatically by itself) will use the information from their database to launch targeted attacks. One of the most simple and entry-level attacks that can be launched with this publicly scraped info is Executive Fraud.
These malicious actors and their automated tools can launch thousands of attacks like this per day. All the attackers must do is let their tool run by itself and wait some someone to respond to their e-mail – or nibble on the bait. Hence, the name “phishing”.
The more information that an attacker has on your company, the more sophisticated the attacks can become. Intelligent attackers will use the executive’s identity to extract non-public information from employees at the company and use this information to further advance the sophistication of their attack.
Ultimately, the attacker’s goal is usually to extract a ransom payment from you, sell your information to the highest bigger on the dark web, or commit corporate espionage.
How to block executive fraud.
NOTE: If you’re not an IT Professional, have your IT Department handle this for you by sending them this article.
Unlock the Full Potential of Microsoft 365 for Your Business Guide
Are you using Microsoft 365 but feel like there’s more you could be doing with it? Our easy-to-follow eBook shows you how to get the most out of the tools you already have. Whether you want to save time, work better with your team, or just make your day a little easier, this guide is for you. Download it for free — just enter your email to get instant access and start making the most of your Microsoft 365 Suite.

Step 1. Login to your Microsoft 365 Admin portal (https://admin.microsoft.com)
Step 2. Navigate to “Exchange Admin Portal”, a new tab will open
Step 3. On the left navigation pane, click “Mail Flow” > “Rules”
Step 4. Click “Add a rule” > “Create a new rule”
Step 5. Give the rule an appropriate name. Apply this rule if “The Sender” “has specific properties including any of these words” > A new tab will expand:
Step 6. Under “Select user properties” select “DisplayName”. For the value, enter the name of the executive that is being impersonated. For this example, we used our CEO, Reid McConkey:
Step 7. Click save and return to the main rule creation pane. Under “Do the following” select “Block the message” and configure and rejection settings you want. We recommend “delete the message without notifying anyone.”
Step 8. Configure exceptions for the real executive’s e-mail addresses to ensure they won’t be blocked. Set “Except if” to “The Sender” “address includes any of these words” and enter in the executive’s legitimate e-mail addresses, including any personal addresses or secondary corporate e-mail addresses they may send e-mail to the company from.
Step 9. Click Save.
You’re done – going forward, anyone who e-mails your domain with the same display name as your executive, it will be automatically blocked. This obviously has some potential flaws, especially if your CEO’s name is James Jones – but it’s free, so can you really complain?
(For Microsoft 365 customers without access to Microsoft Defender for Office 365, such as M365 Business Standard or E3)
1. Login to your Microsoft Defender portal at https://security.microsoft.com
Step 2. Go to the anti-phishing page: https://security.microsoft.com/antiphishing and edit your existing anti-phishing policy. If a non-default policy doesn’t already exist, click “Create” to open the new anti-phishing policy wizard. Name it appropriately then click Next.
Step 3. Identify the internal recipients that the policy applies to. Select your entire domain and click Next.
Step 4. Under “Impersonation” check “Enable users to protect” > click “Manage 0 sender(s)” and add your executive users to this list.
Step 5. Optionally, enable domain-wide protection and add trusted senders and domains. It is also highly recommended that your IT department maintain a whitelist of trusted senders to avoid legitimate mail being caught in the spam filter. We also recommend enabling spoof intelligence.
Step 6. Click next. Configure how strong you want these policies to be. We recommend starting out by simply moving the message to the recipients’ junk folders. If you’re not an IT professional, leave the rest of the settings alone. If you are an IT professional, use your own discretion here.
Step 7. Review & submit your new policy. Make sure it’s turned on. Keep an eye on the mail flow log for any e-mails that are being flagged by this, and make sure they aren’t legitimate senders.
(For Microsoft 365 customers with access to Microsoft Defender for Office 365, such as M365 Business Premium or E5)
Great – I’ve blocked all executive fraud for good… right? (Conclusion)
Well… not totally accurate. I wish it were true, but these policies are good for blocking only a good portion of executive fraud e-mails, not all of them. This means that employees still need to be trained on how to spot these types of threats with regular cybersecurity training, and safeguard policies need to be put in-place to ensure requests are legitimate.
As AI and other more sophisticated impersonation methods become more prevalent, this problem will only worsen. If there’s one thing you take away from this article, it’s this: You can and should be doing the above actions to block a good amount of the volume of these attacks, but training and good operational security in the form of safeguard policies are still mandatory.